About
About This Demonstration
This instant demonstration illustrates how the Cisco Secure Workload solution addresses security challenges by providing unprecedented insights, hybrid-cloud workload protection, and comprehensive workload protection across a multicloud infrastrcture.
Limitations
-
Because this is an instant demo, customization of the environment may not be retained for future connections.
-
Sessions are limited to a maximum of 2 hours.
-
Throughout this guide, there may be slight differences between the screen shots and your environment since the Secure Workload exists in different dCloud datacenters.
Requirements
The table below outlines the requirements for this preconfigured demonstration.
| Required | Optional |
|---|---|
|
Laptop Cisco.com Login to dCloud |
About This Solution
The technological changes over the last few years has made it challenging for enterprises to secure the modern workloads and applications.
Workloads can run anywhere: It is now common for an enterprise to have not only a data center or two (or more), but also many remote locations with server assets, as well as one or more cloud infrastructure partners. The data center perimeter today contains the data center, remote mini-data centers, and cloud infrastructure partners.
Heterogeneous nature of the workloads: Workload types in an enterprise environment not only include bare-metal servers and virtual machines, but also more dynamic ones such as containers and microservices. These are managed and operated using different technologies.
Applications are constantly changing: Today’s applications are dynamic, with new versions and changes coming very often, and they can also scale in and scale out depending on business needs. Some applications scale out into a public cloud environment to support increased traffic.
Opening up of new attack vectors: With the diminishing perimeter as workloads expand to public cloud environments and users increasingly becoming mobile, the attack surface also changes. With more rapid application development occurring in more places, more often, there are more software vulnerabilities. As traffic shifted inside to east/west, where there is little to no segmentation, malicious code can now roam freely inside the trusted intranet.
Because these trends and changes drive new security initiatives and requirements for applications and workloads across a multicloud environment, Cisco has created Cisco Secure Workload™ expressly to meet these requirements. Cisco Secure Workload enables the security objectives of CXOs and executives, while enabling disparate teams to work together using a single platform that can meet the workload security requirements of app developers, security architects, and SecOps.
Recent years have seen a relentless pace of change and digital acceleration across industry verticals. Some trends include:
-
Business trends: High-performing application and security integrity are top of mind for CXOs due to their growing online presence.
-
People and process trends: Teams are asked to work together efficiently to support and meet service levels for the business, giving rise to the terms “DevOps,” “DevSecOps”, and “NetDevOps”.
-
Technology trends: As applications become increasingly critical to the business, new requirements for visibility, security, workload protection, and service operations in this complex environment have emerged.
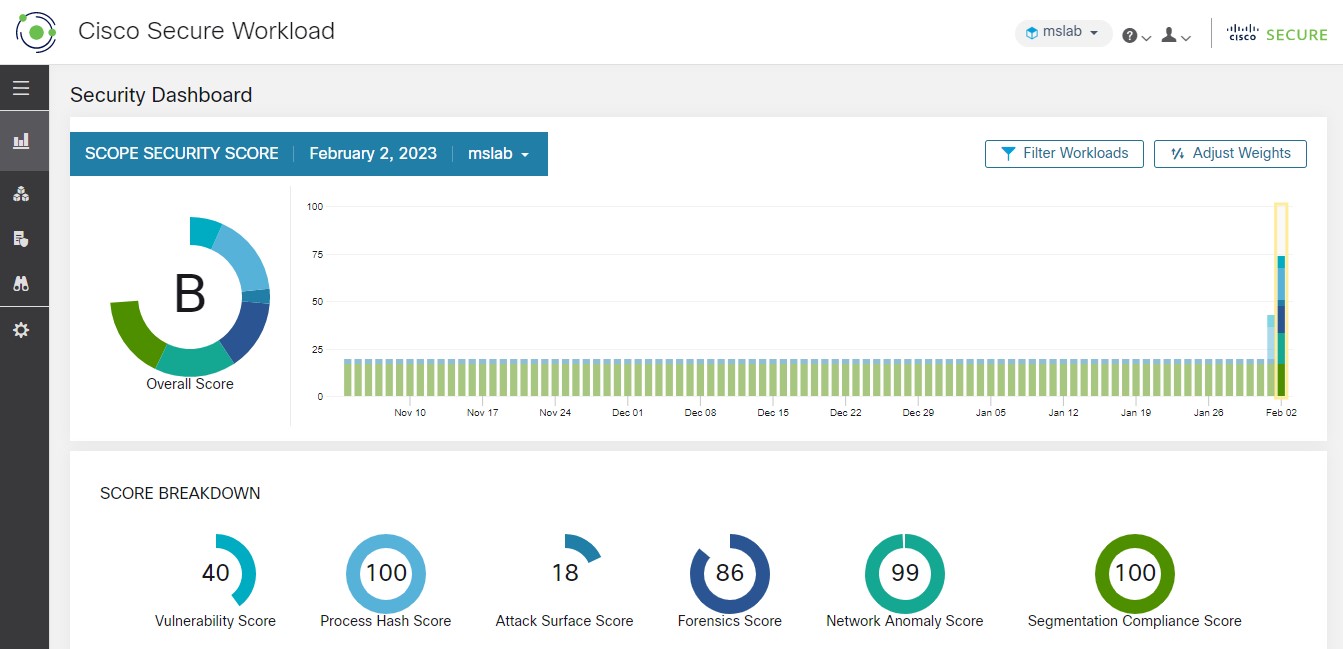
Cisco Secure Workload represents a paradigm shift that leverages machine learning and big-data analytics to address the modern data center and has the following characteristics: (1) it is multicloud, where boundaries extend beyond on-premises data centers; (2) it has heterogeneous environments with a combination of bare-metal hosts, virtualized workloads, and containers; and (3) it is dynamic to meet the changing application behavior and workload lifecycle. By leveraging algorithmic approaches, Cisco Secure Workload is able to automate the identification of application behavior and map microsegmentation policies, across private data center, cloud, and hybrid deployments at a level of detail required to support security capabilities, and added business value.
The high-level architecture is illustrated below.

Cisco Secure Workload is an open platform that is accessible via GUI, REST API, and an event notification framework. Operators may even leverage the compute and storage of the platform to write their own user apps in Python or Scala. The open APIs and event notification bus are leveraged by Secure Workload ecosystem partners for integration with SIEM, CMBD, and other tools.
In summary, Cisco Secure Workload is purpose built to address industry trends impacting our customers’ businesses. The solution leverages streaming telemetry, behavior analysis, unsupervised machine learning and artificial intelligence, and big data analytics to deliver pervasive visibility, automated intent-based policy, workload protection, performance management, and much more. As a unified platform, Cisco Secure Workload allows various teams to work together efficiently across organizational silos and integrates with an ecosystem of partner solutions to increase value throughout the IT data center environment.
Use Cases
Cisco Secure Workload main use cases:
-
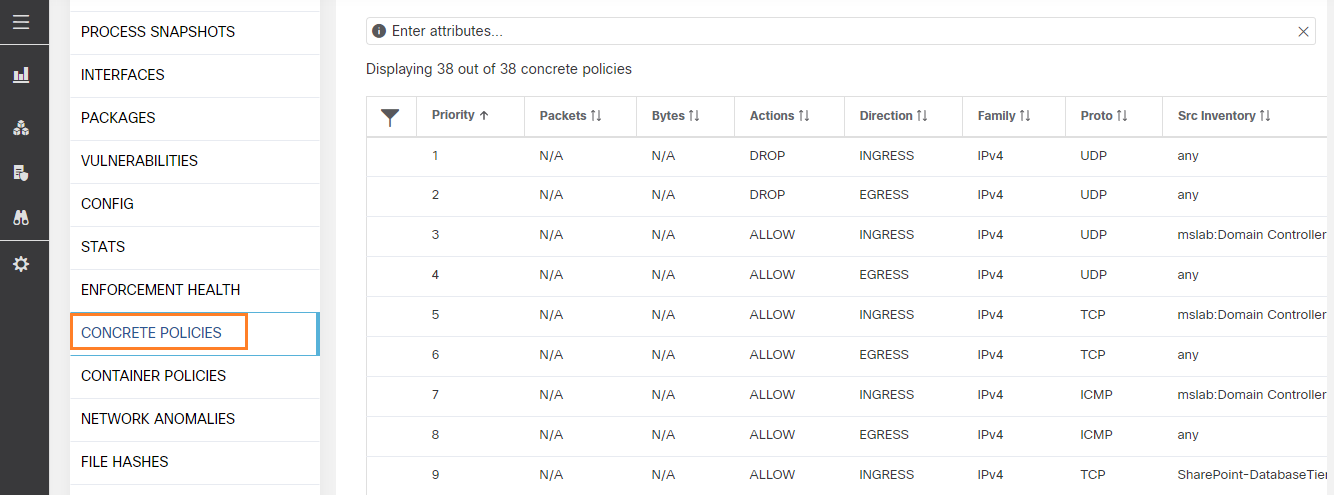
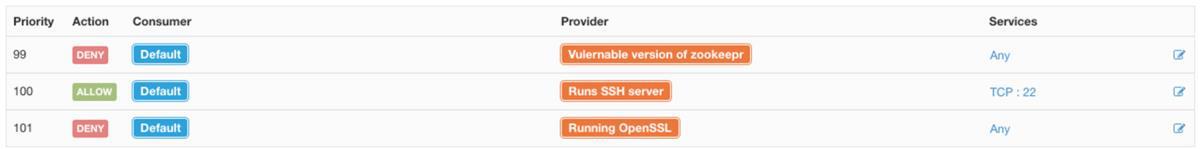
Microsegmentation: Cisco Secure Workload enables security teams to implement a secure, zero-trust model for workloads using microsegmentation. It automates the policy generation for microsegmentation using unsupervised machine learning and near real-time application behavior analysis. It normalizes this policy based on the priority and hierarchy before enforcing it. These policy elements are enforced for an application using the operating system firewall capabilities such as ipsets and iptables, in the case of Linux servers, and the Windows advanced firewall, in the case of Microsoft Windows servers. This approach delivers a stateful and consistent segmentation across multicloud data centers at scale. It also allows you to minimize lateral movement in case of security incidents. Additionally, in a virtualized and container environment, this mechanism ensures that segmentation policy moves with the workload, allowing increased application mobility without the need for an infrastructure-specific segmentation policy. As application dependencies and communication patterns evolve, Cisco Secure Workload helps ensure that the policy is updated automatically.
-
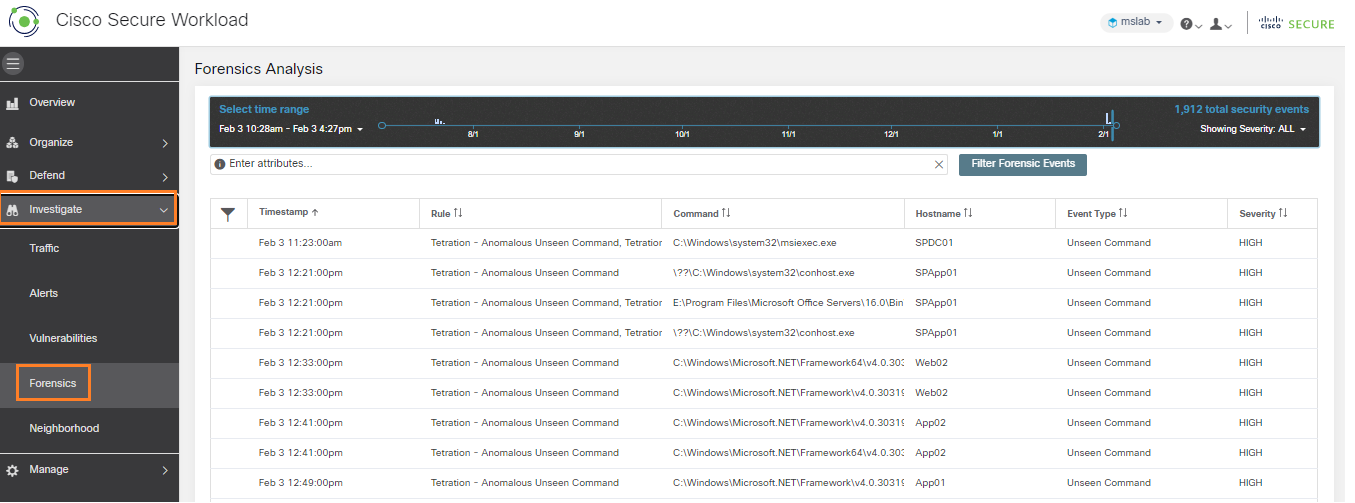
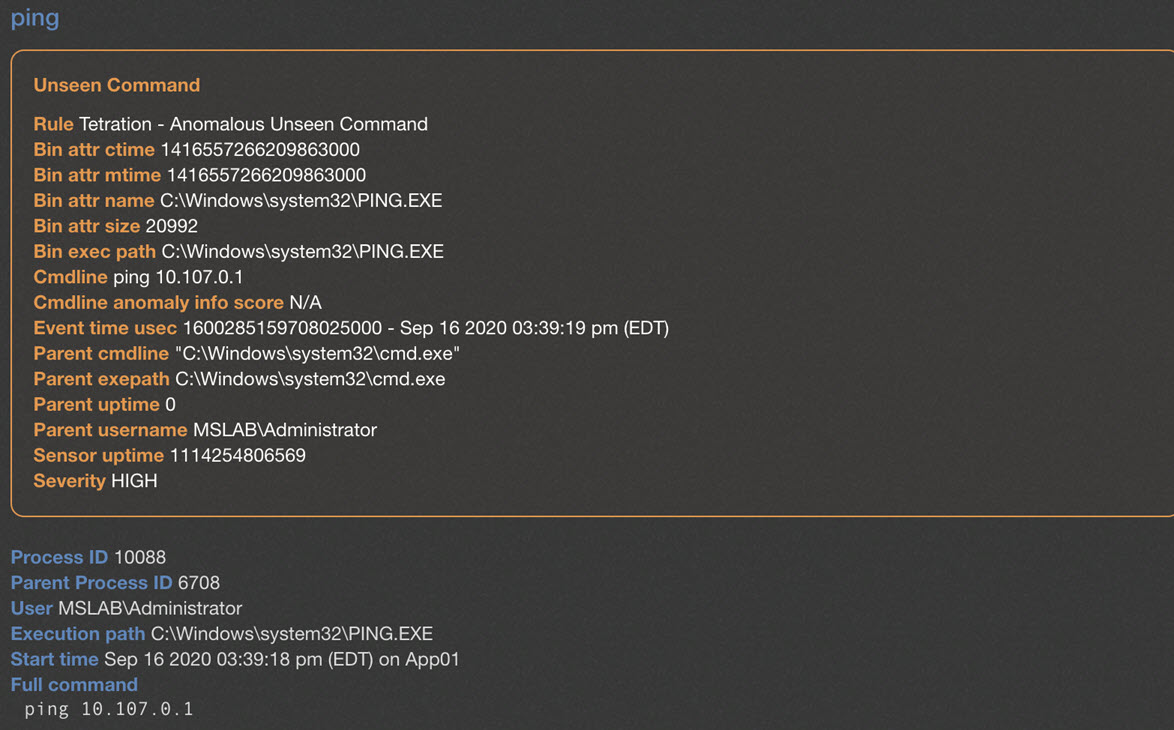
Workload anomalous behavior detection: Data center workloads are deployed for a specific activity or a function. Therefore, workload behavior could be baselined and proactively detect anomalous behaviors. To achieve this, Cisco Secure Workload monitors the process and communication activities on the workloads. It can detect various malicious behavior activities like:
-
Privilege escalations
-
Shell-code executions
-
MITRE-identified techniques and tactics
-
Side-channel attacks
-
Unseen commands
In this way, security operations can quickly identify indicators of compromise and take remediation steps to minimize the impact.
-
-
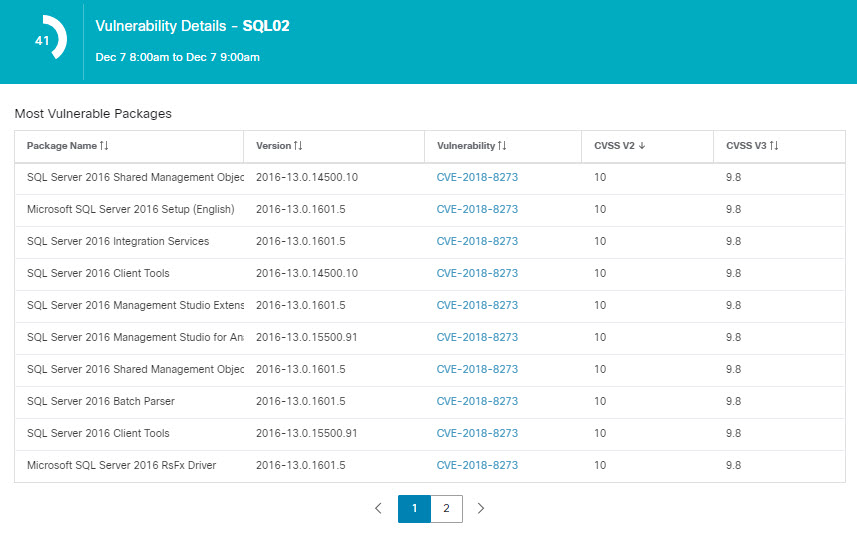
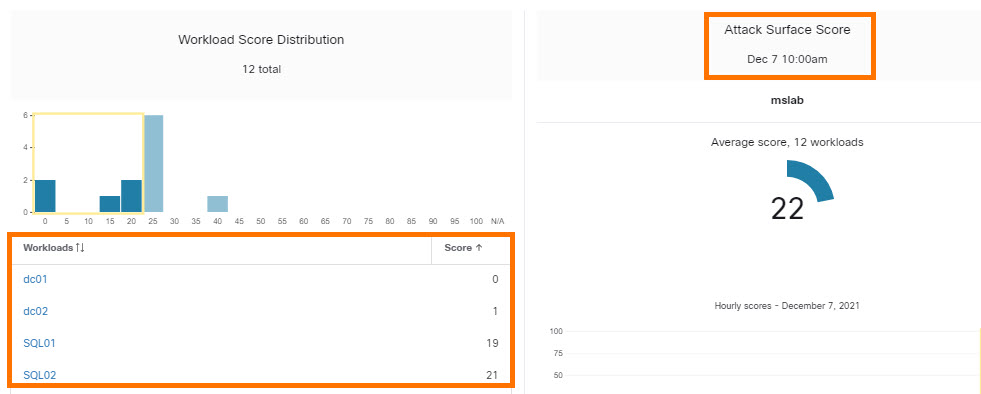
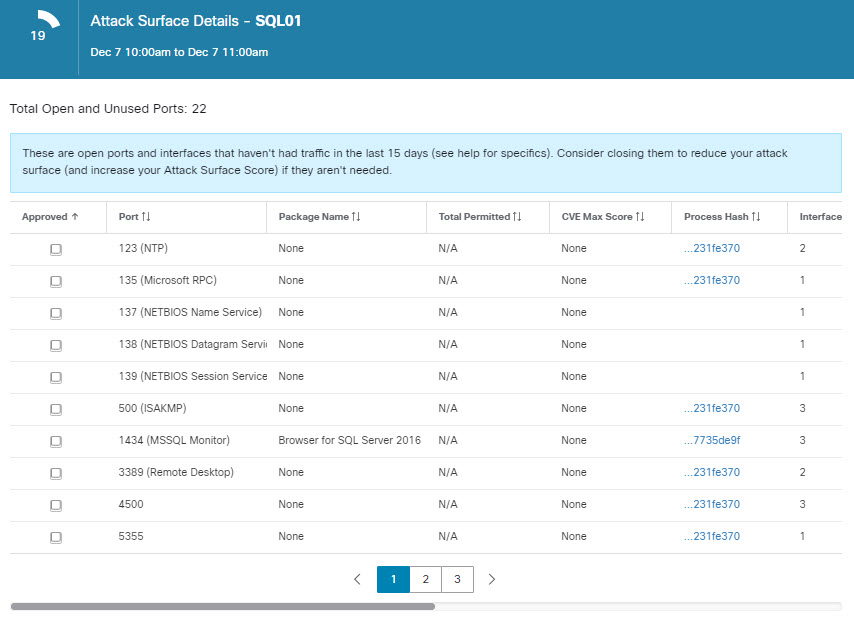
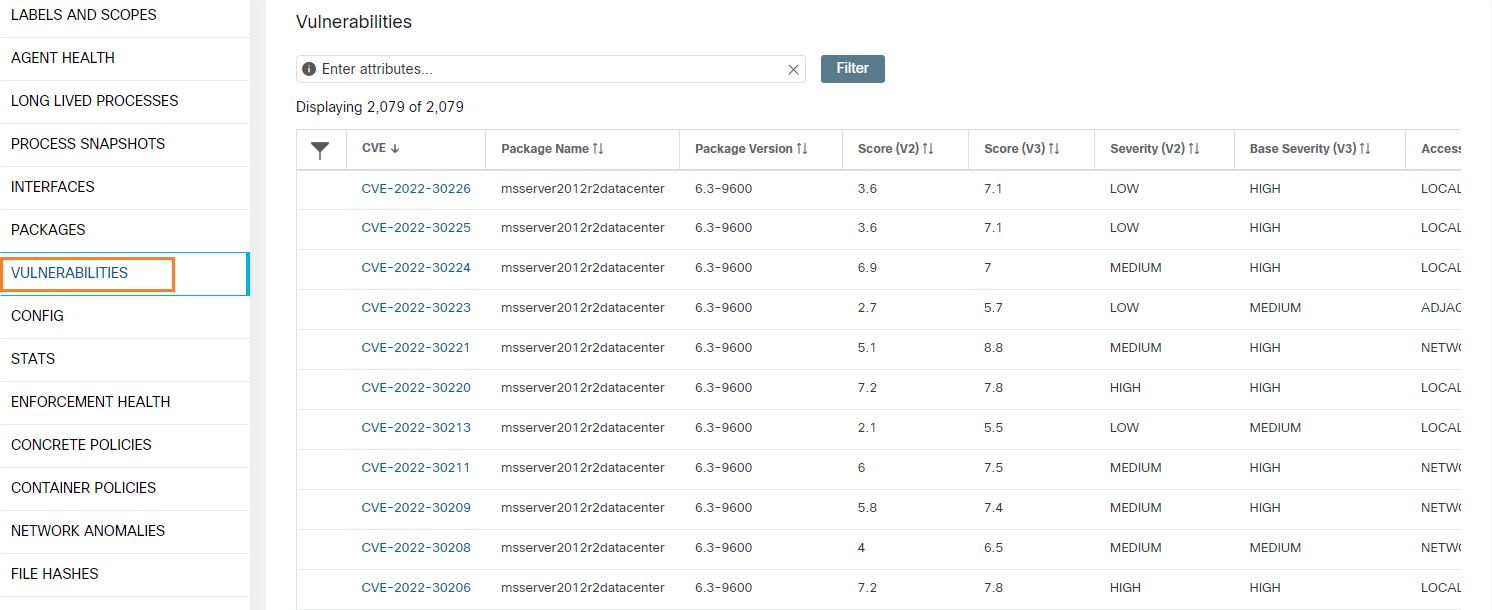
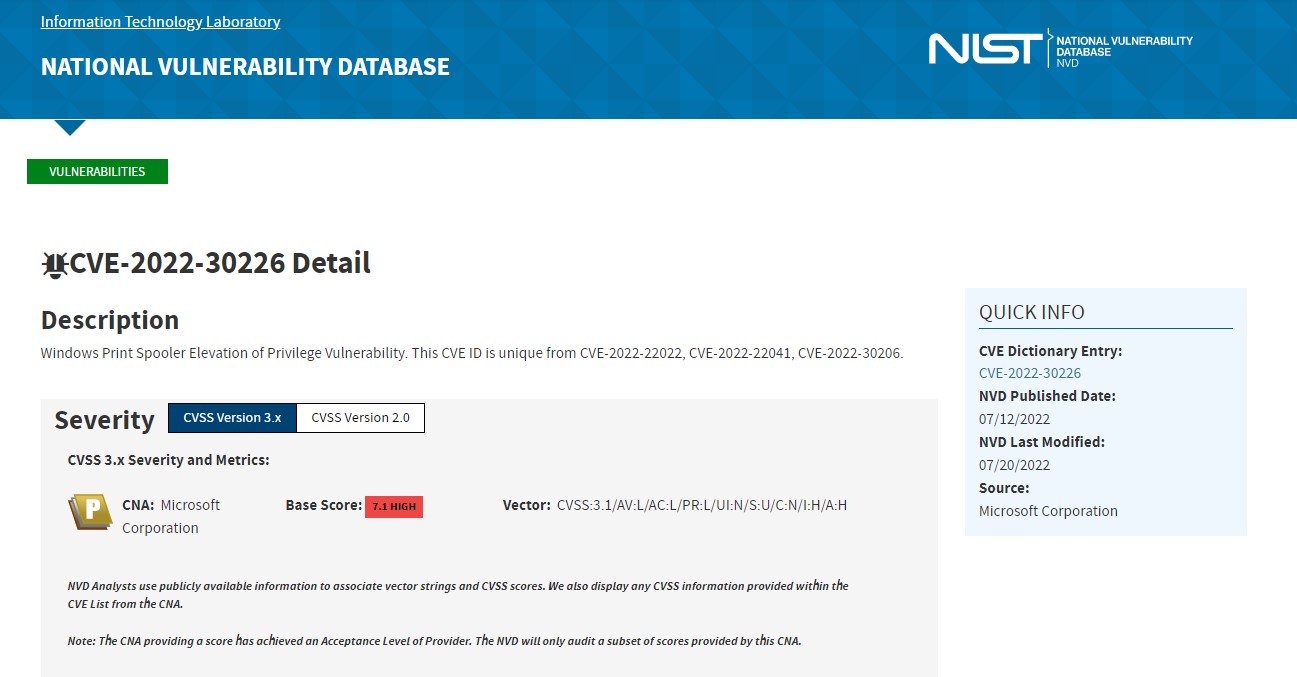
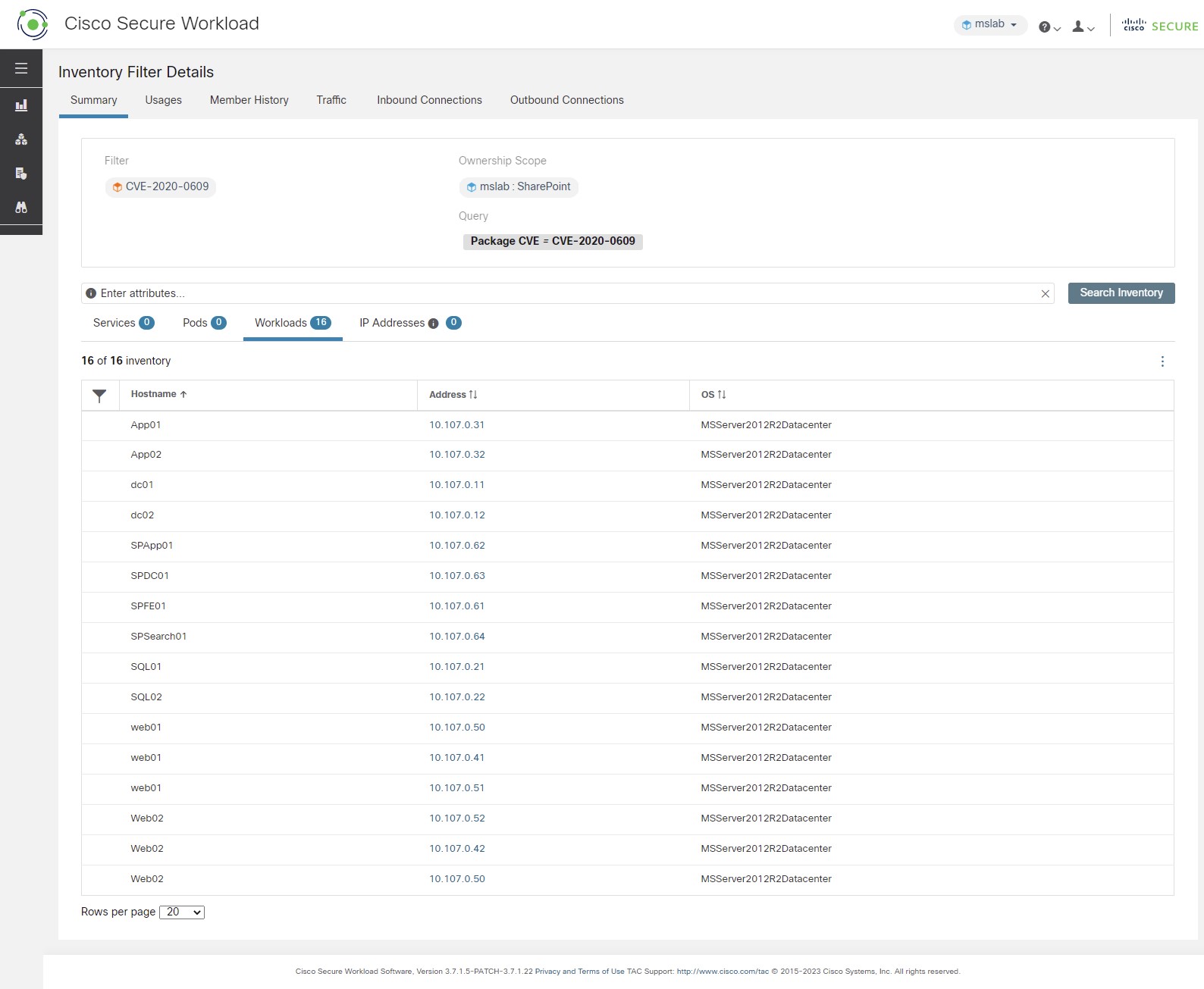
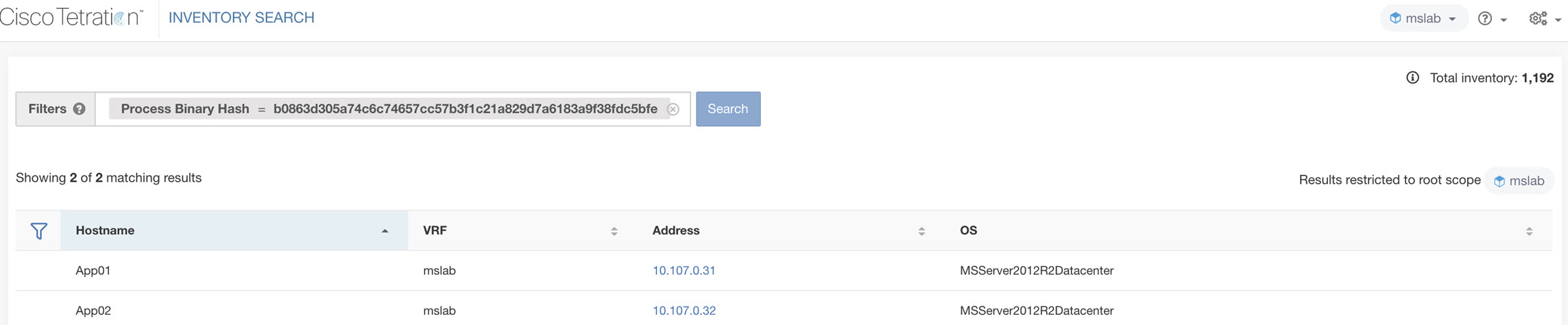
Reducing the attack surface: Attack surfaces are introduced in the data center due to vulnerabilities associated with the software packages, OS versions, and due to the stale ports and processes running in the environment. Cisco Secure Workload, in real time, identifies the full inventory of all software packages installed on the workloads and provides the ability to detect common vulnerabilities and exposures associated with these packages. It also provides actionable security insight where administrators can define policies to quarantine or restrict communication of workloads when certain vulnerabilities are detected. Additionally, it also identifies those open ports with process bindings that are not used. This concrete information helps administrators determine if something can be safely shutdown to reduce the exposure.
There are three layers in the architecture:
-
Telemetry and policy enforcement: Cisco Secure Workload primarily uses software agents to collect telemetry from the workloads as well as to enforce microsegmentation policies. These agents can be deployed across heterogeneous environments, in public or private clouds, across virtual machines, to containers, and bare-metal servers. Additionally, Cisco Secure Workload integrates natively with other systems to get workload context information. These systems include orchestration platforms (VMWare vCenter, Kubernetes, and so on), IP address management systems, DNS servers, CMD systems, and so on.
-
In certain environments where software agents cannot be used, Cisco Secure Workload offers other mechanisms to collect telemetry from workloads such as ERSPAN mechanisms, NetFlow, IPFIX, or telemetry from load balancers, and so on. Microsegmentation policy enforcement in these environments could be done through infrastructure elements such as firewalls.
-
Analytics and security: The telemetry and the system context from tens of thousands of agent sources are sent securely to the Secure Workload big-data platform, which analyzes the data, using unsupervised machine learning and behavior analysis. The relationships among the workloads and behavior baselining of the workloads are derived. The algorithmic approach and machine learning employed by Cisco Secure Workload results in the workload protection use cases of implementing microsegmentation, identifying workload behavior anomalies, and reducing the attack surface.
About the Application Used in this Lab Environment
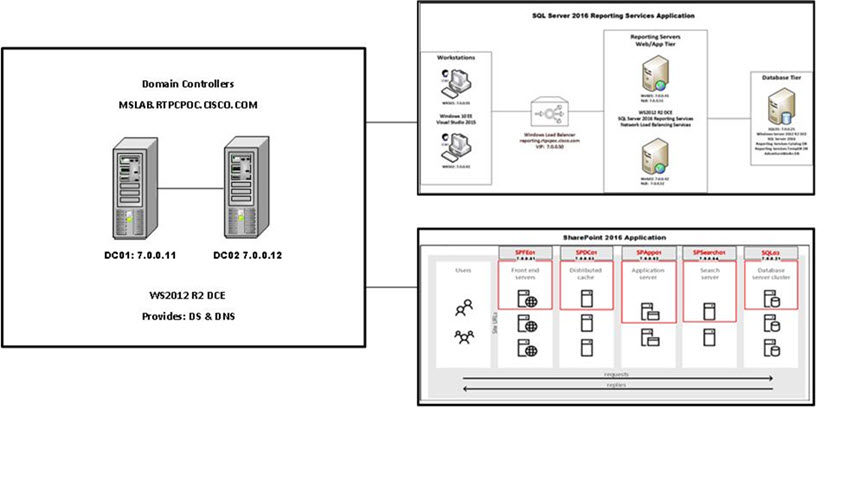
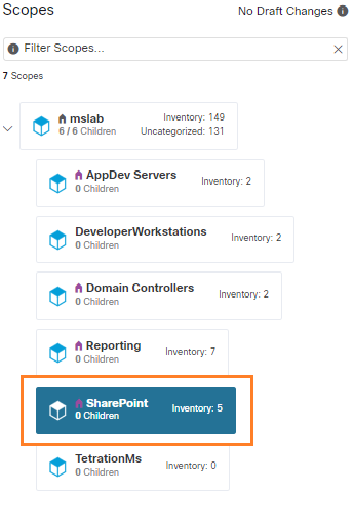
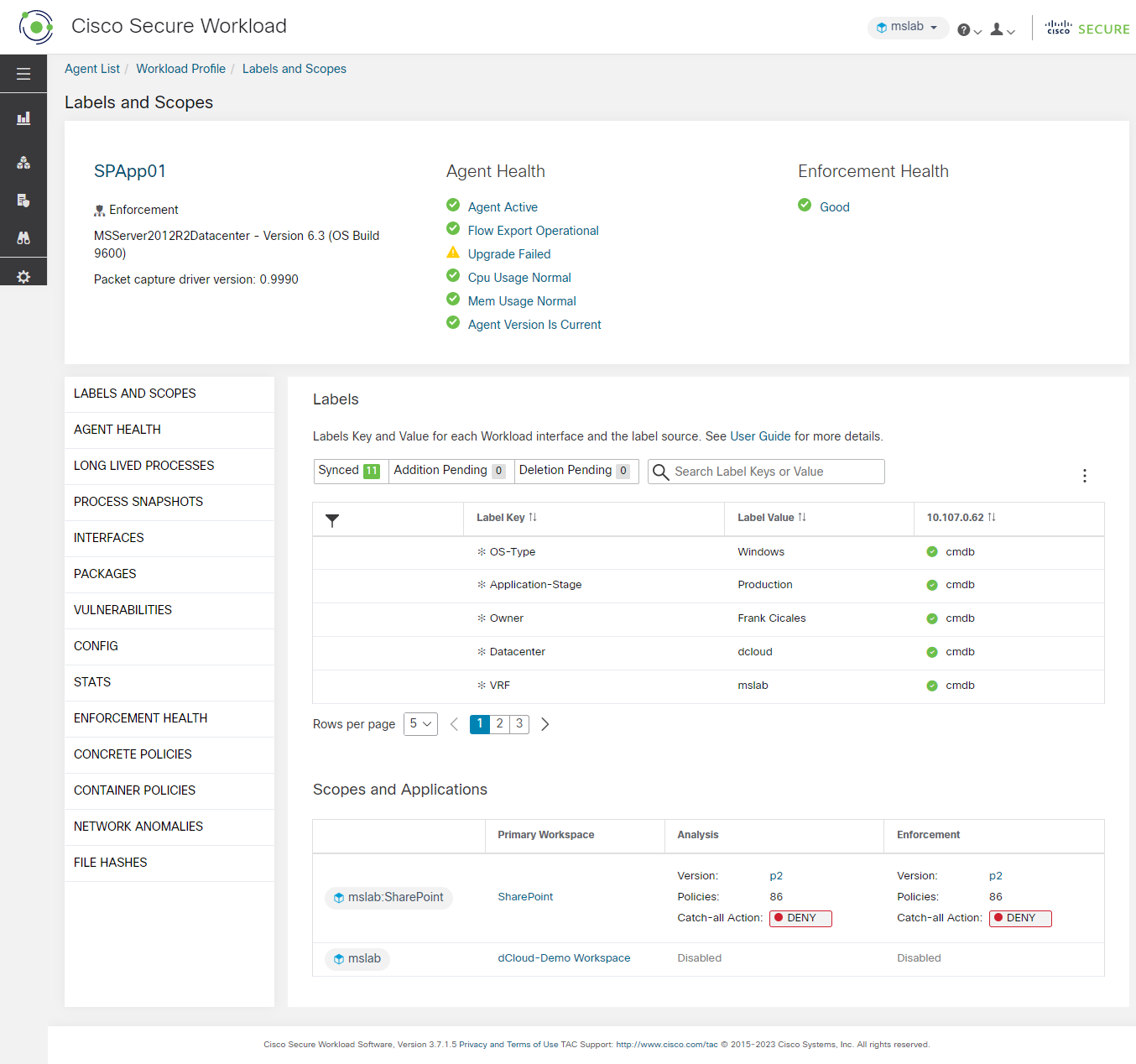
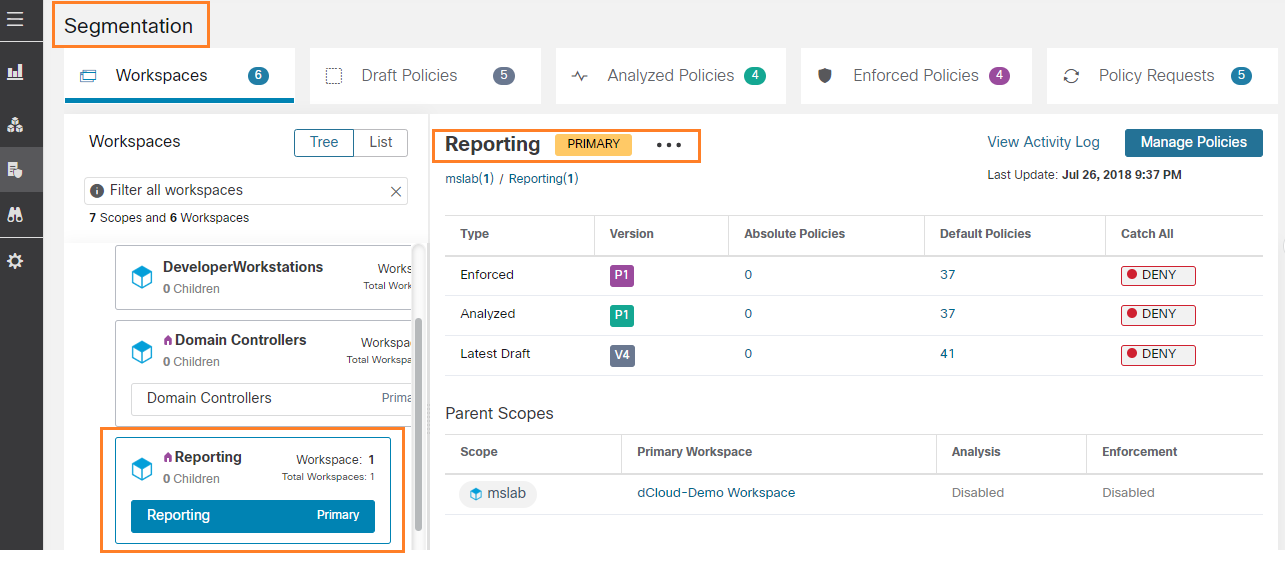
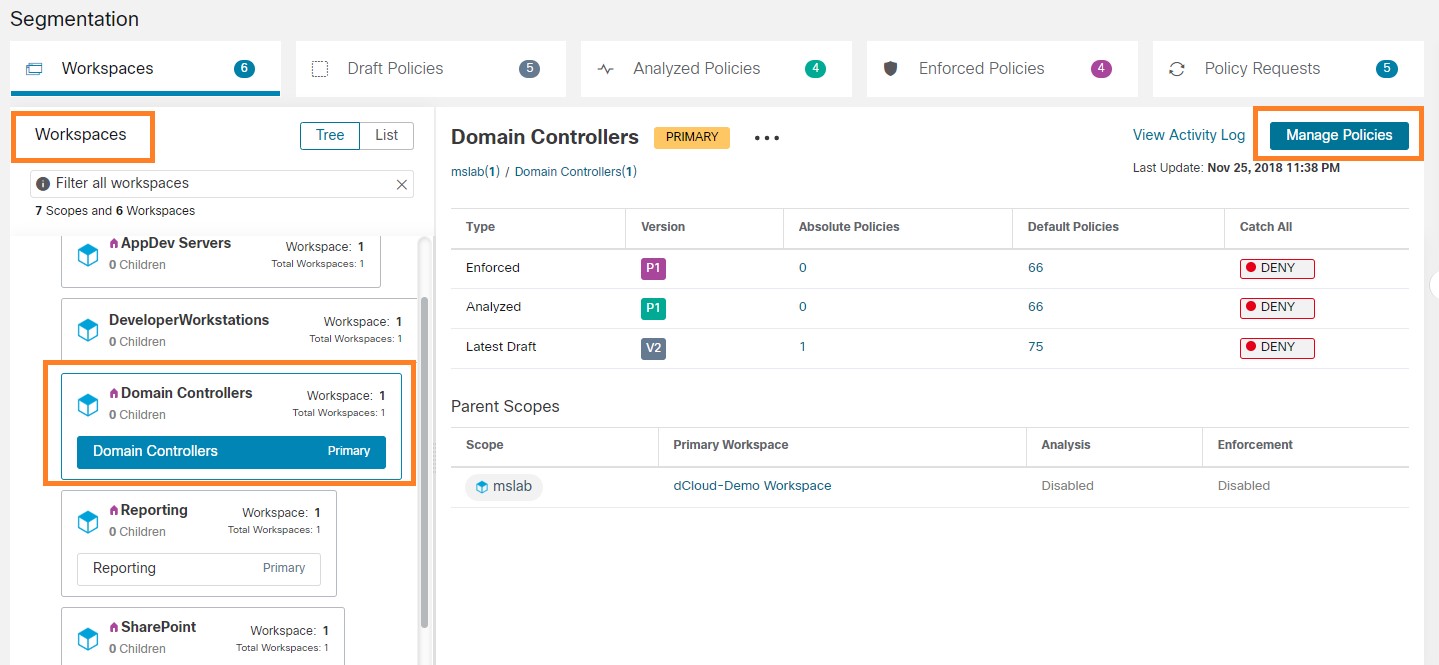
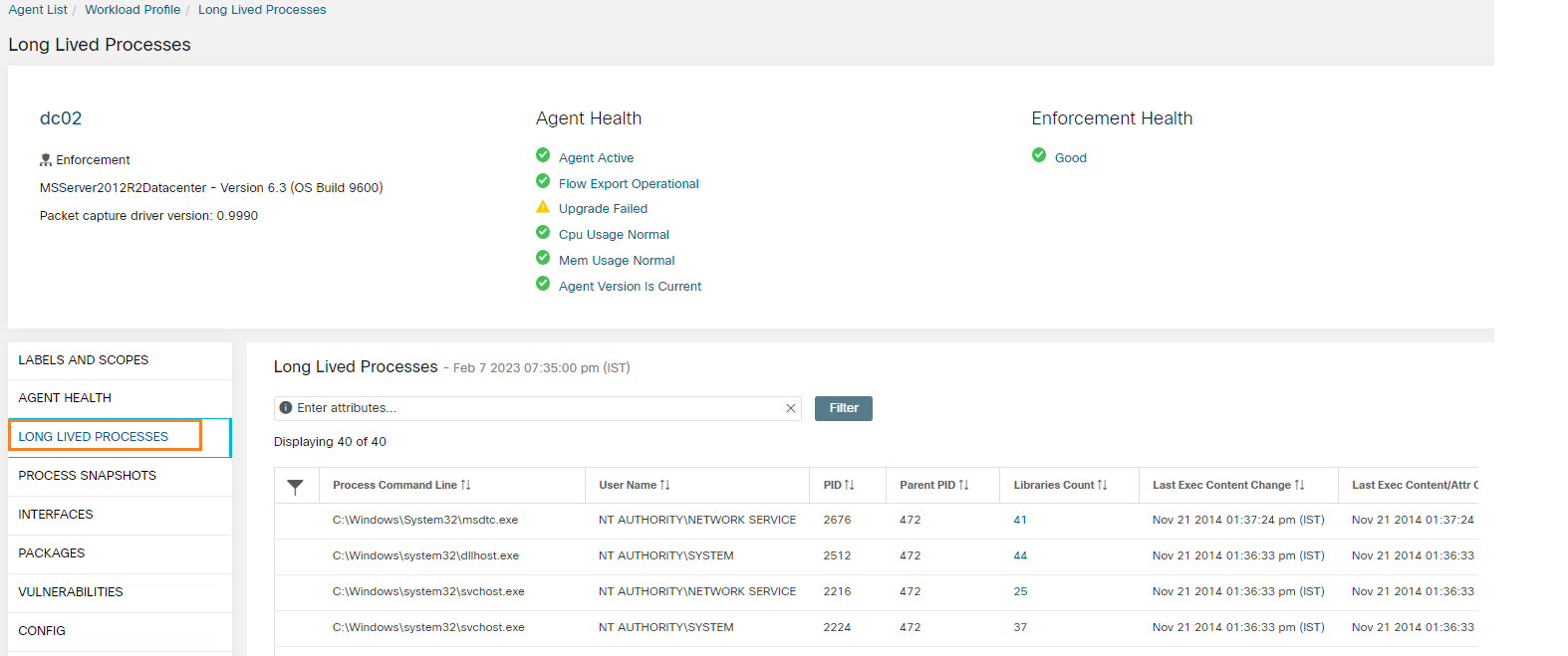
A Microsoft Windows domain has been built for this dCloud experience. There are five application workspaces being monitored by Secure Workload.
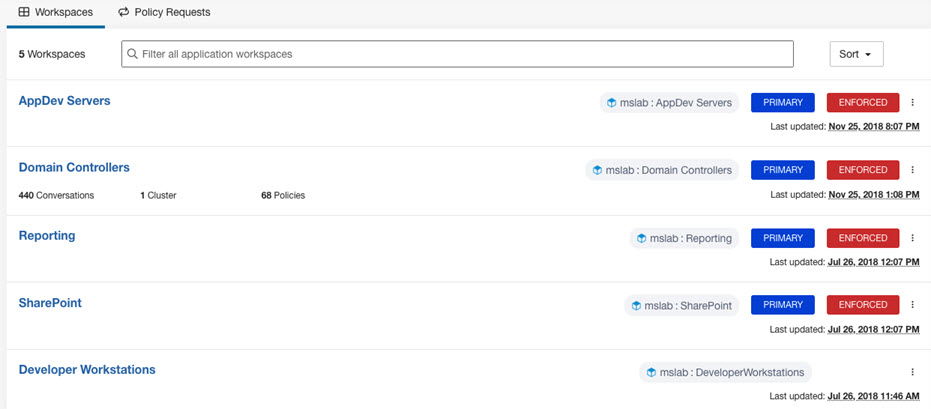
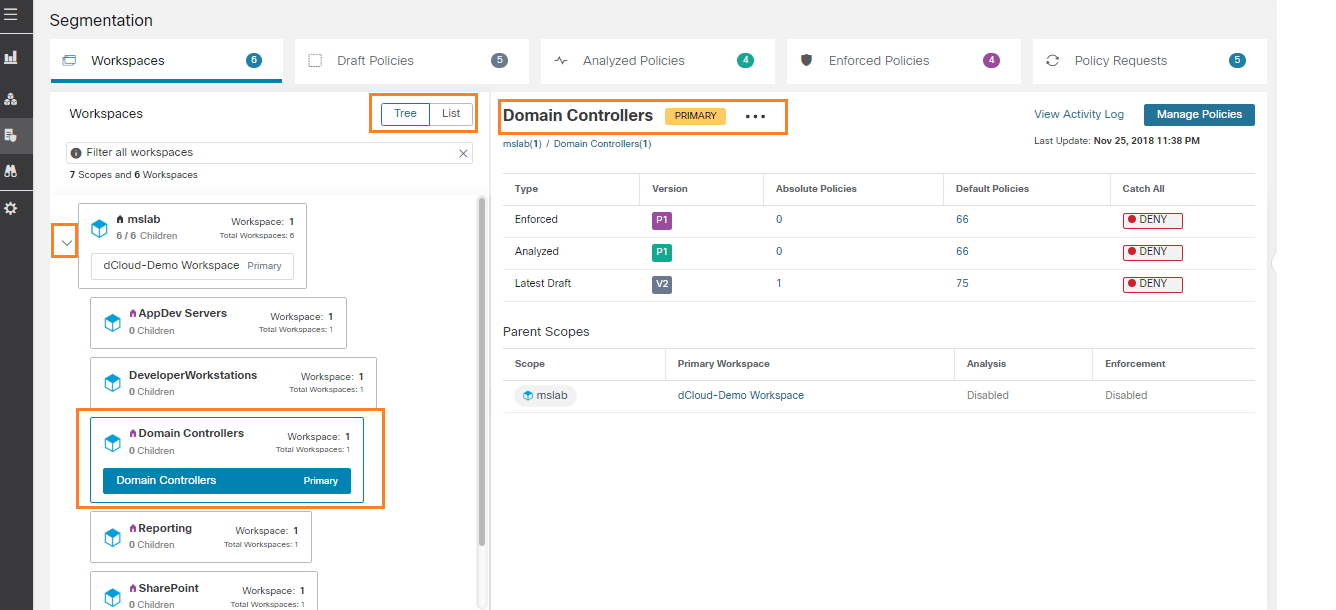
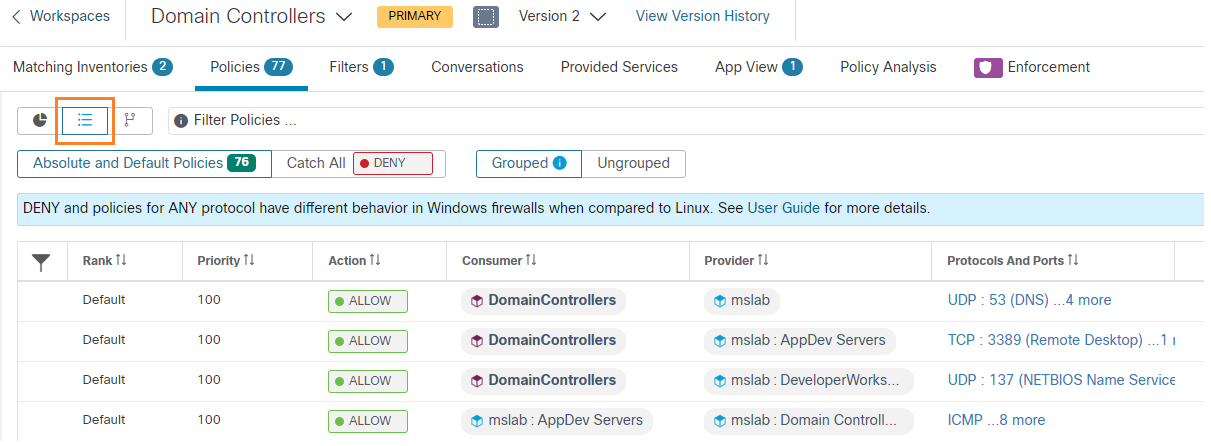
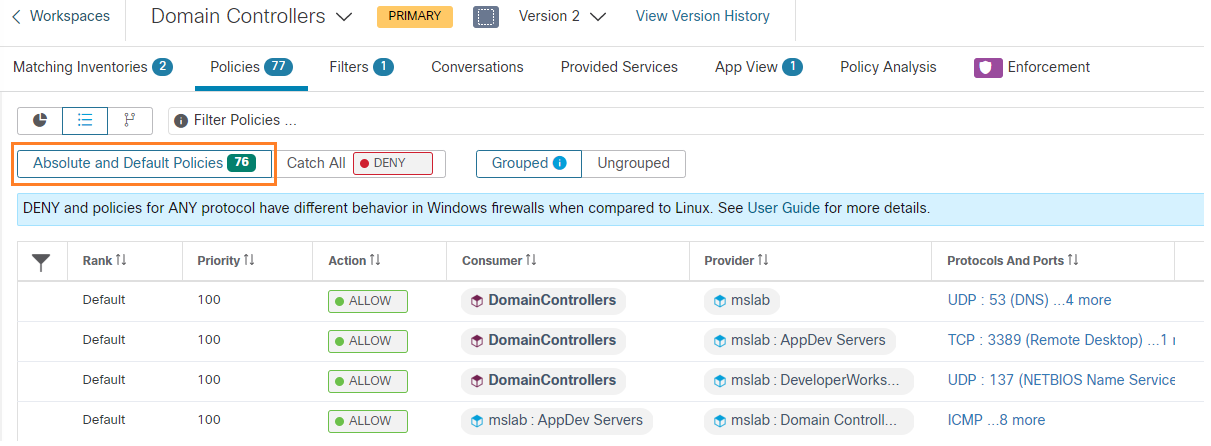
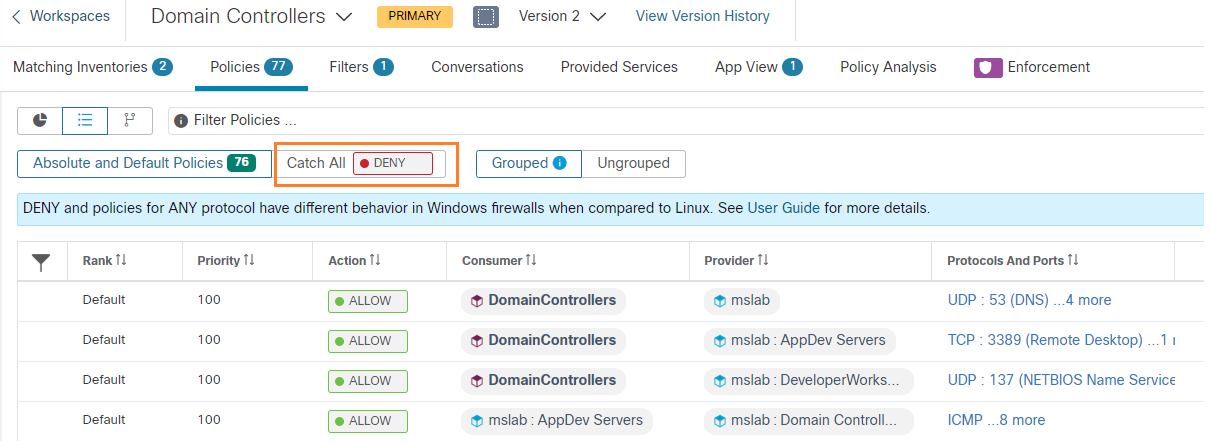
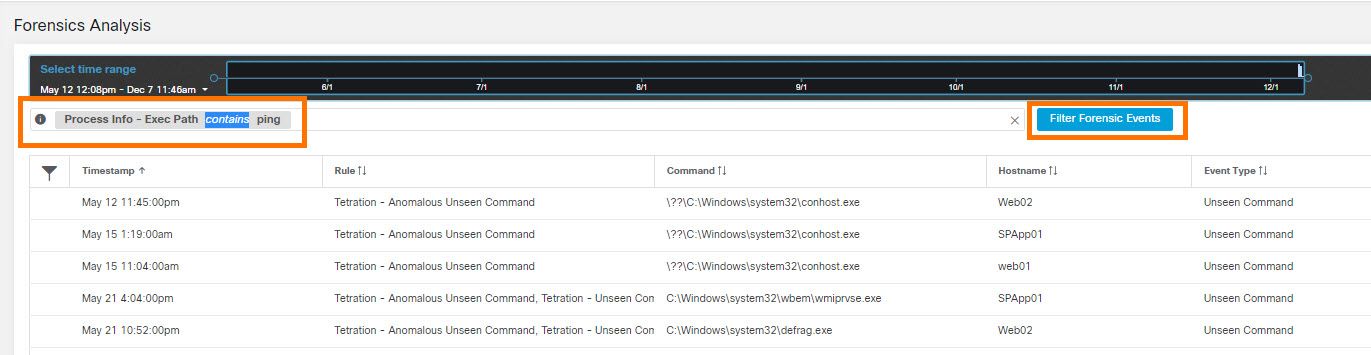
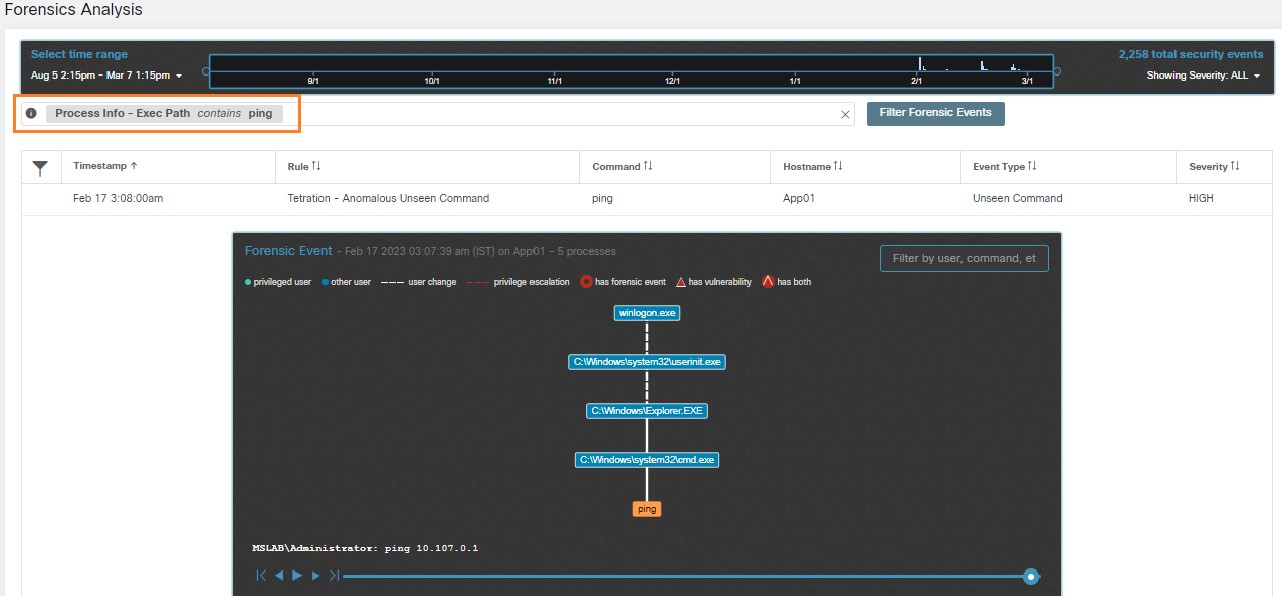
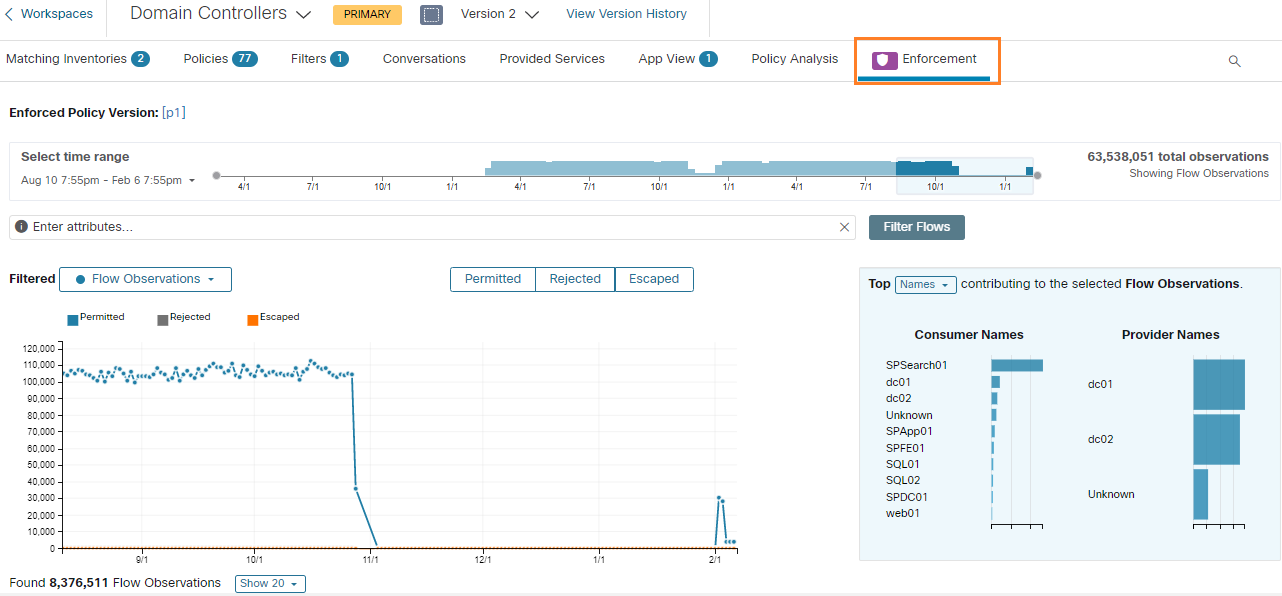
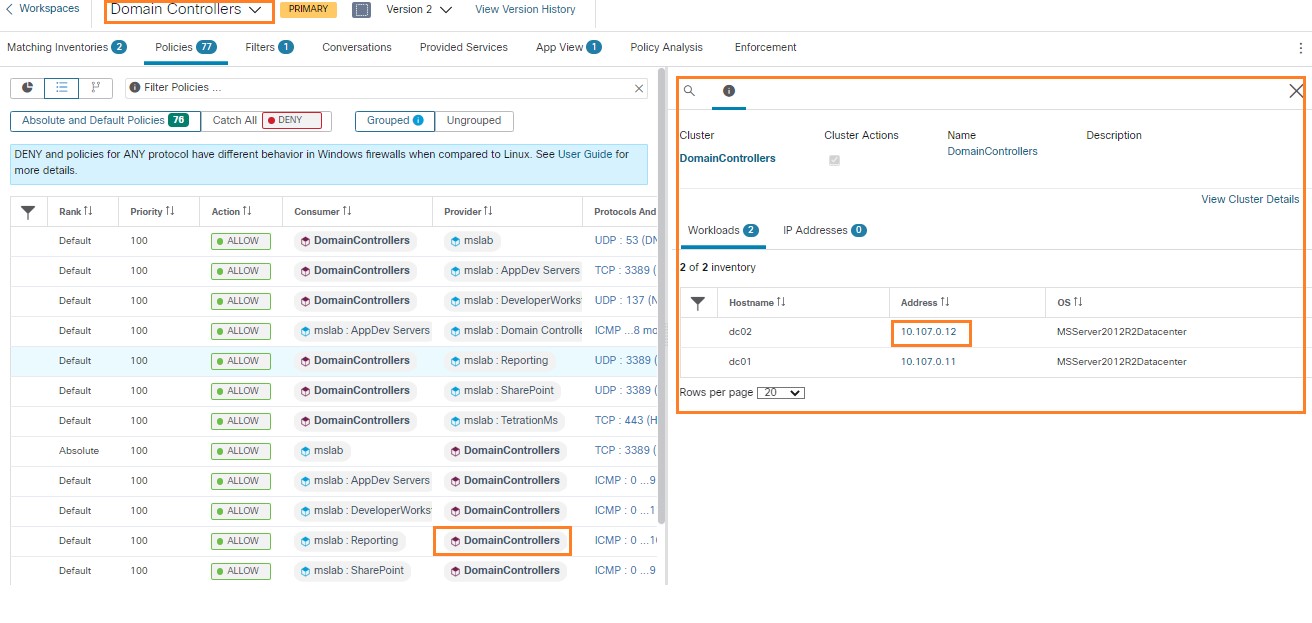
There are Domain Controllers in the Microsoft Windows domain, highlighted in the following image.
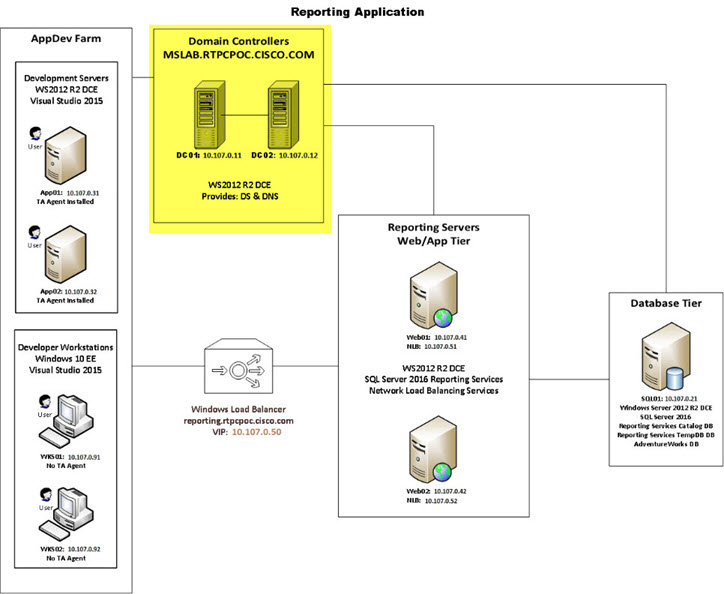
User interaction with the solution dashboard occurs on application development servers with TA agents installed on them, and developer workstations with no agents installed. These are highlighted in the following image.
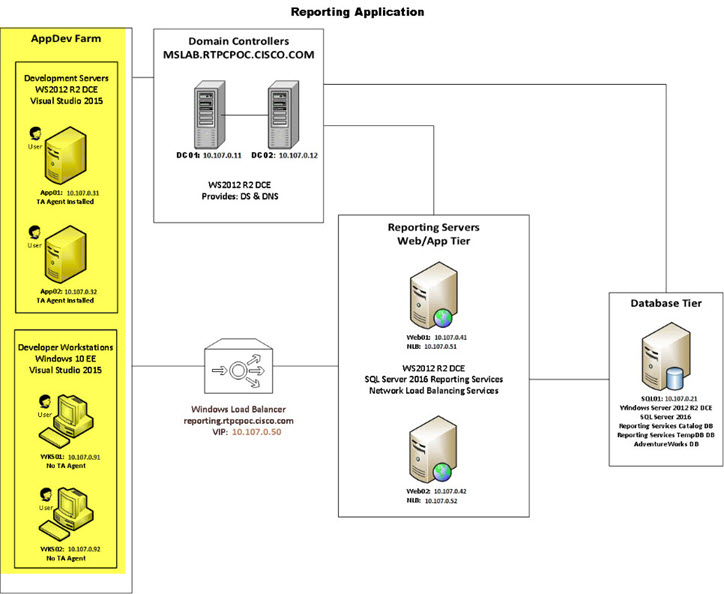
The servers and workstations access the Reporting Servers (the Web and App tier of the reporting application) through a software load balancer, highlighted in the following image.
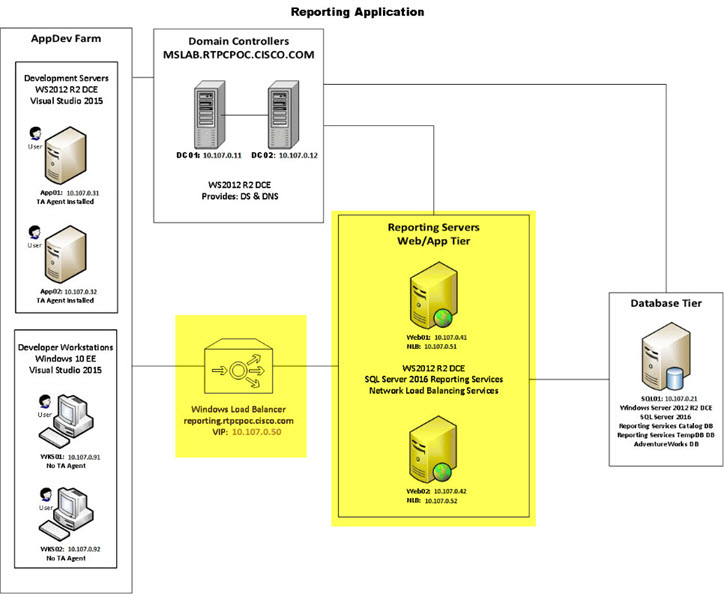
The Web and App tier report data from the database tier, highlighted in the following image.

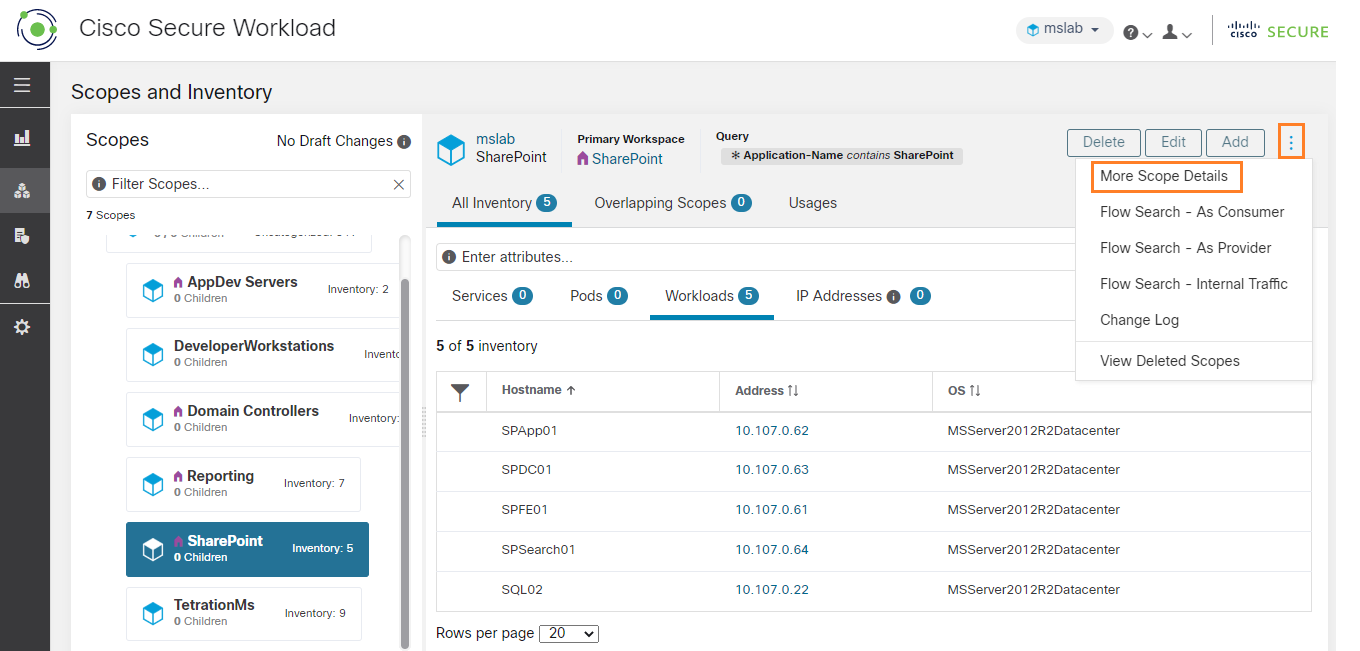
The Sharepoint services also access the domain controllers, separately from the other workspaces.